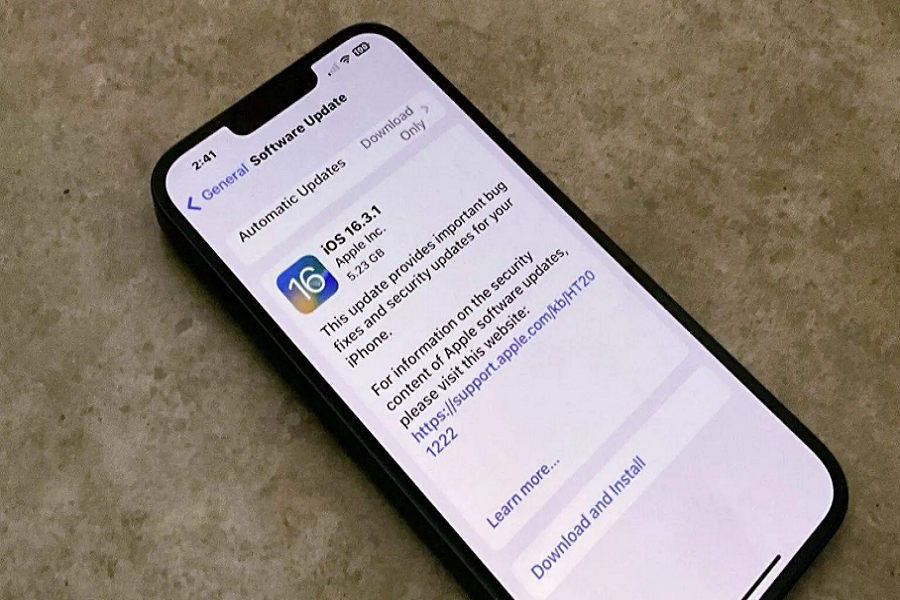
Apple has released iOS 16.3.1 update, although it is not much big of an update, we did receive some security updates along with some enhancements. IOS 16.3.1 had some bug fixes and critical security updates that made it an essential upgrade for iOS users. In this article, we will dive into everything you need to know about the iOS 16.3.1 security updates and how they can help you protect your personal information and enhance your overall experience. From iOS 16.3.1 security update to the latest enhancements, we will explore all the key improvements. So, without further ado, let’s get started and take a closer look at the latest iOS 16.3.1 security update, how it improves your privacy, and everything else you need to know about it.
Apple has not yet given any specific details or mention anything in its release notes about what are the bug fixes in iOS 16.3.1. And it might seem odd but Apple has its reasons for not revealing details about the update. It is to give enough time to people to upgrade their devices and to keep attackers out of reach until then, so they won’t get any information before even updating the device. What I think is that Apple is playing smart. Let us get into details about iOS 16.3.1 security updates.
Kernel Impact: An app may be able to execute arbitrary code with kernel privileges Description: A use after free issue was addressed with improved memory management. CVE-2023-23514: Xinru Chi of Pangu Lab, Ned Williamson of Google Project Zero WebKit Impact: Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. Description: A type confusion issue was addressed with improved checks. WebKit Bugzilla: 251944
CVE-2023-23529: an anonymous researcher
WebKit
Impact: Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.
Description: A type confusion issue was addressed with improved checks.WebKit Bugzilla: 251944
CVE-2023-23529: an anonymous researcher
There are two major corrections: Every Apple device that can run iOS/iPadOS 16 contains a kernel hole that could have allowed an app to run arbitrary code with kernel privileges. This flaw has been repaired, as has a Safari flaw that might have allowed arbitrary code execution from a malicious web page.
The latter vulnerability “may have been actively exploited,” according to the notes, leaps to the top of the list and necessitates the release of iOS 16.3.1. Security holes are frequent, however, it’s crucial to repair your device as soon as possible if an exploit has already been discovered in the wild.
The problem addressed in iOS 16.3.1, which is logged as CVE-2023-23529, could allow an attacker to run code on someone’s iPhone. The iPhone manufacturer continued, “Apple is aware of a report that this problem may have been actively exploited.”A second significant security flaw in the Kernel, the core component of the iPhone operating system, is also fixed by Apple iOS 16.3.1. The vulnerability, identified as CVE-2023-23514, might let an attacker use an app to run arbitrary code with Kernel privileges. There have been no reports of the problem being leveraged in attacks, as far as Apple is aware.According to information displayed on Apple’s support page, the alreadyexploited hole is in WebKit, the engine that powers the Safari browser from the maker of the iPhones.
Until next time, with another topic. Till then, Toodles.