Introduction
The perception that macOS Malware systems are largely immune to malware has been challenged by the emergence of sophisticated threats. One of the most concerning developments is the discovery of Cthulhu Stealer, a malware specifically designed to target macOS users. This malware is engineered to steal sensitive information, including passwords, web browsing data, and cryptocurrency wallet credentials. As cybercriminals increasingly exploit vulnerabilities in macOS, understanding Cthulhu Stealer’s functionality and the risks it poses is crucial for users seeking to protect their data.
Recent Released: Disney Plus Involving Environment Iceland With New 3D
What is Cthulhu Stealer?
Cthulhu Stealer is a newly identified malware that operates as a malware-as-a-service (MaaS), available for rent at a price of $500 per month. This service allows malicious actors to easily deploy the malware against unsuspecting users. Cthulhu Stealer disguises itself as legitimate applications, such as CleanMyMac, Adobe GenP, and even popular games like Grand Theft Auto IV, to trick users into installation. Once installed, it employs various tactics to extract sensitive information from the victim’s device.
Basic Features of Cthulhu Stealer
- Targeted Data Collection: The malware is designed to collect a wide range of sensitive information, including:
- User Credentials: System and MetaMask passwords.
- iCloud Keychain Data: Saved passwords and sensitive information stored in the Keychain.
- Web Browsing Information: Cookies and saved passwords from browsers like Chrome and Safari.
- Cryptocurrency Wallet Information: Credentials from various wallets, including MetaMask, Coinbase, and Binance.
- Application Data: Information from apps such as Telegram and gaming accounts.
- Data Exfiltration: Cthulhu Stealer compresses the stolen data into a ZIP file and sends it to a command-and-control (C2) server for the attackers to access.
Distribution Method
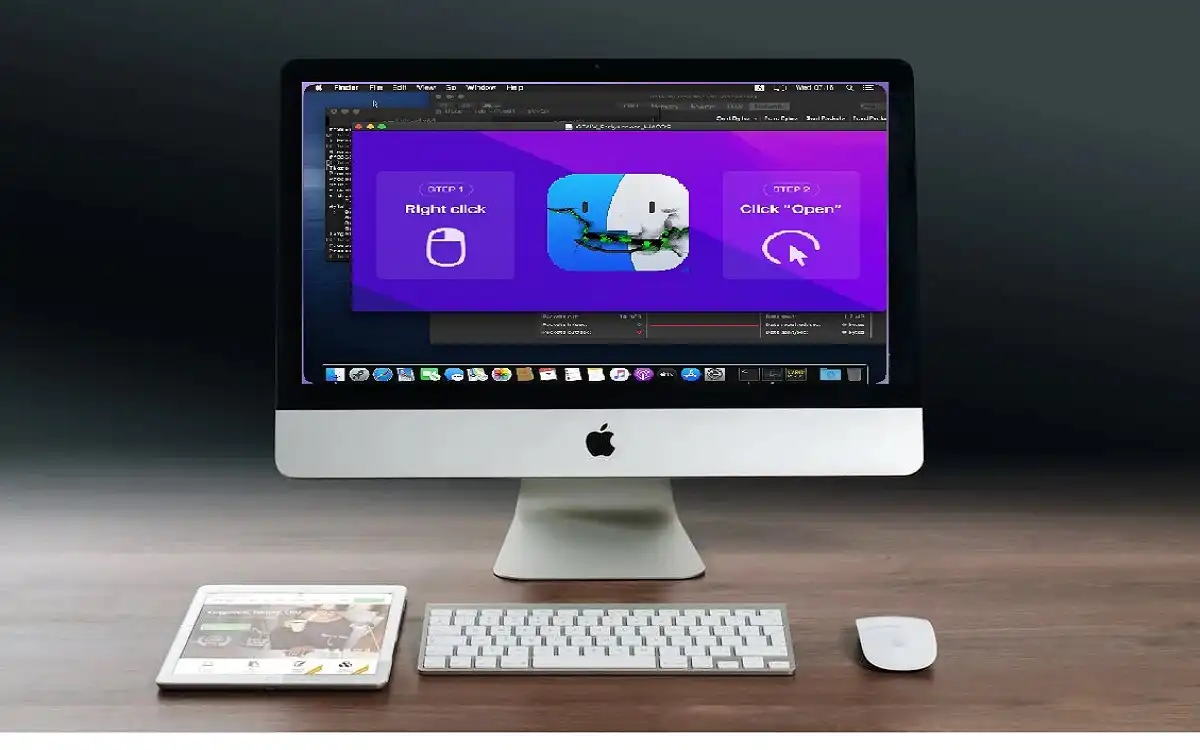
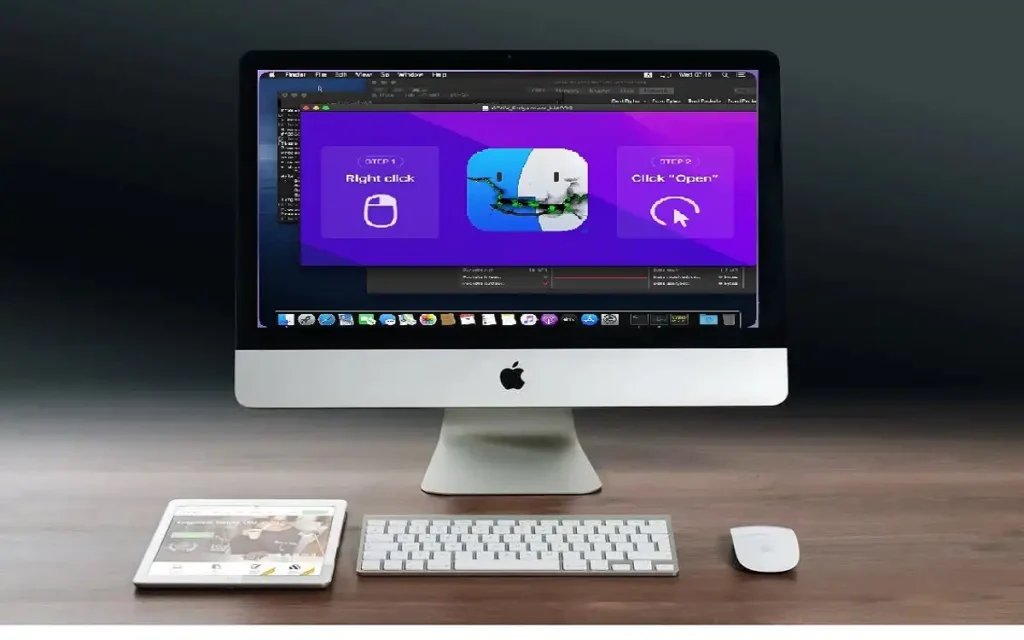
Cthulhu Stealer is distributed via Apple disk image (.dmg) files, which contain binaries optimized for both ARM and x86_64 architectures. When users mount the disk image, they are prompted to enter their system password using macOS’s osascript utility, a common tactic among various macOS malware strains. After obtaining the system password, the malware further prompts the user for their MetaMask password, allowing it to harvest a wealth of sensitive information.
Functionality and Data Theft
Cthulhu Stealer’s primary goal is to harvest sensitive data from infected macOS devices. Here’s a detailed overview of the specific types of information that the malware collects:
1. User Credentials
- System Passwords: The malware prompts users to enter their macOS system passwords.
- MetaMask Passwords: Specifically targets users of the MetaMask cryptocurrency wallet.
2. iCloud Keychain Data
Utilizes an open-source tool called Chainbreaker to dump passwords stored in the iCloud Keychain, which includes:
- Saved Passwords: Credentials for various applications and websites.
3. Web Browsing Information
Cthulhu Stealer collects data from web browsers, which includes:
- Cookies: Extracts cookies from browsers, allowing attackers to hijack user sessions.
- Saved Passwords: Credentials saved in browsers like Chrome and Safari.
4. Cryptocurrency Wallet Information
The malware targets a variety of cryptocurrency wallets, including:
- MetaMask
- Coinbase
- Binance
- Wasabi
- Electrum
- Daedalus
- Trust Wallet
- Blockchain Wallet
- Dapper Wallet
- Coinomi
- XDeFi
5. Application Data
Cthulhu Stealer is capable of collecting information from various applications, such as:
- Telegram: Gathers account details and cookies from Telegram, which can include sensitive messages and contacts.
- Gaming Accounts: Targets user data from gaming platforms such as Minecraft and Battle.net.
6. System Information
The malware collects detailed information about the infected system, including:
- Operating System Version: Identifies the version of macOS running on the device.
- IP Address: Obtained through services like ipinfo.io, helping attackers tailor their strategies.
- System Name and Hardware Specs: Information about the device’s configuration and specifications.
7. Data Packaging and Exfiltration
Once the malware has gathered the sensitive information, it compresses the data into a ZIP file, which is then sent to a command-and-control (C2) server. This ZIP file may include:
- A record of the user’s country code.
- A timestamp of when the data was collected.
Current Status and Recommendations
Reports suggest that the original developers of Cthulhu Stealer have ceased operations due to internal disputes and accusations of scams within the cybercriminal community. However, the malware remains a significant threat as it can still be utilized by other malicious actors.
Recommendations for macOS Users
To protect against such threats, macOS users are advised to:
- Download Software Only from Trusted Sources: Use the Mac App Store or official websites.
- Be Cautious of Applications Requesting System Passwords: Always verify the legitimacy of applications requesting sensitive information.
- Keep Operating Systems and Applications Updated: Regularly update macOS and applications to ensure the latest security patches are applied.
Steps to Take if Your macOS System is Compromised by Cthulhu Stealer
If you suspect your macOS system has been compromised by Cthulhu Stealer, it’s crucial to take immediate action to mitigate the damage and prevent further data loss. Here are the steps you should take:
- Disconnect the Computer from the Network: Prevent further data exfiltration by disconnecting from the internet.
- Do Not Run Any Commands or Take Further Actions on the Compromised System: Avoid actions that may destroy forensic evidence.
- Contact the Information Security Team: Report the suspected compromise to your organization’s information security team.
- Cooperate with the Investigation: Follow the instructions of the information security team during their investigation.
- Avoid Sharing Details of the Compromise: Maintain confidentiality to protect the integrity of the investigation.
- Refrain from Contacting Law Enforcement: Any communication with law enforcement must be coordinated with the information security team.
Finally
Cthulhu Stealer exemplifies the growing trend of malware targeting macOS users, emphasizing the need for vigilance and robust security practices. As cybercriminals continue to develop more sophisticated methods to exploit vulnerabilities, it is essential for users to remain informed and proactive in protecting their data. By adhering to best practices for software downloads, being cautious about password prompts, and keeping systems updated, macOS users can mitigate the risks posed by threats like Cthulhu Stealer.
| Feature | Details |
| Type of Malware | Cthulhu Stealer |
| Target OS | macOS |
| Cost | $500 per month (malware-as-a-service) |
| Data Collected | User credentials, iCloud Keychain data, web browsing info, cryptocurrency wallet information, etc. |
| Distribution Method | Disguised as legitimate applications (e.g., CleanMyMac, Adobe GenP) |
| Current Status | Original developers reportedly inactive, but malware remains a threat |
Staying informed about emerging threats like Cthulhu Stealer is crucial for maintaining the security of personal and sensitive information on macOS devices.