Cisco’s Internetwork Operating System (IOS) XE software that runs on various Cisco routers and switches has recently been found to contain multiple critical security vulnerabilities. These vulnerabilities could allow cyber criminals to take control of affected devices or crash them, leading to serious implications for companies and organizations using vulnerable Cisco devices.
Privilege Escalation Flaws Enable Takeover
Among the most severe vulnerabilities uncovered in IOS XE are privilege escalation flaws that could enable full system compromise.
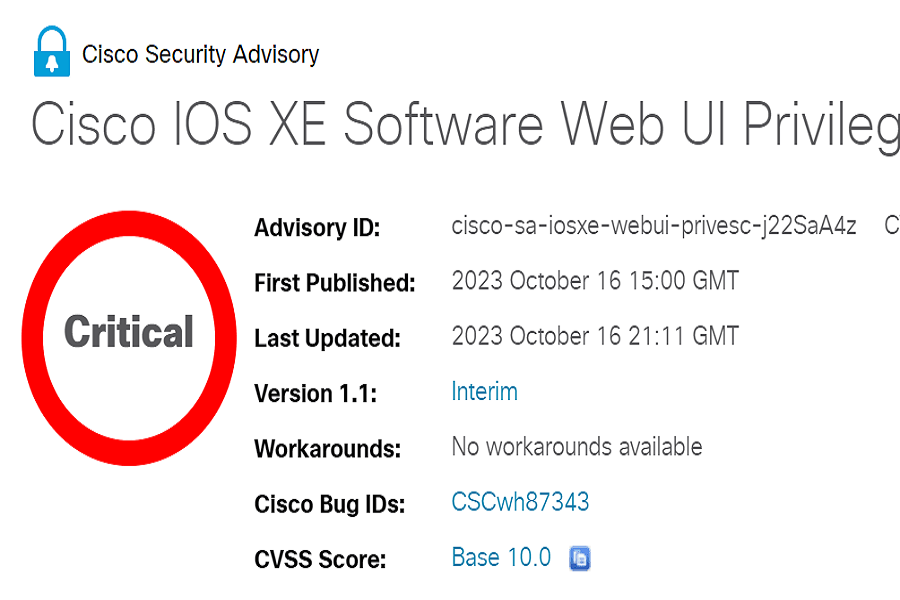
One such flaw, tracked as CVE-2023-20198, exists in the web UI feature of IOS XE. This vulnerability can be exploited by an unauthenticated attacker to create a privileged account on the system with complete control. Both physical and virtual Cisco devices running IOS XE are affected if they have the web UI enabled.
Another privilege escalation vulnerability resides in the Cloud Management for Catalyst migration tool in IOS XE. Here, an authenticated local attacker could gain root privileges by modifying Meraki registration parameters. This is due to insufficient memory protection.
Both flaws allow attackers to create accounts with the highest level of system access, enabling remote takeover and manipulation of the network device.
Command Authorization Bypass Leads to Data Theft
A further vulnerability discovered in the AAA feature of IOS XE can allow an authenticated remote attacker to bypass command authorization protections.
By exploiting this flaw, an attacker could remotely connect to an affected Cisco device using Secure Copy Protocol (SCP) and exfiltrate data from the file system without authorization. This undermines access controls and enables data theft.
DoS Vulnerabilities Can Crash Systems
On top of command execution and escalation flaws, security researchers also found multiple denial-of-service (DoS) vulnerabilities afflicting IOS XE.
One such vulnerability exists in the AppQoE and Unified Threat Defense components of IOS XE. Here, an unauthenticated remote attacker could trigger a crash leading to system reboot and temporary outage.
A second DoS vulnerability is found in the L2TP feature of IOS XE. This flaw can also be triggered remotely without authentication to crash affected Cisco routers and switches. The result is again a denial-of-service condition.
Applying Mitigations and Software Updates
Cisco has released software updates to address these critical IOS XE vulnerabilities. However, mitigation steps can also reduce exposure, especially where updates cannot be applied immediately.
For the web UI privilege escalation flaw, Cisco recommends disabling HTTP Server on externally facing devices. Monitoring networks for signs of compromise is also advised.
For other vulnerabilities without workarounds, updating IOS XE software to the latest fixed release is strongly recommended by Cisco. The company’s Software Checker tool can help identify exposure.
Conclusion
The privilege escalation, command bypass, and DoS vulnerabilities found in Cisco’s IOS XE software pose significant risk to enterprise networks and devices. Their ease of exploitability makes rapid patching urgent.
All organizations using devices that run IOS XE should audit their exposure to these flaws and apply updates where possible. Extra vigilance is required to detect attempts to compromise networks via these vulnerabilities. Going forward, prompt installation of IOS XE security fixes is essential.
The critical security gaps in such core network software underline the importance of vulnerability management. Cisco customers must ensure they maintain their IOS XE devices at the latest patched levels to avoid potential breaches or outages from these and future flaws.